Ever wondered if your computer is being watched? Do you feel something you installed is tracking you on your computer? There is always a chance that harmful software installed on your PC is reported to a hacker.
One time or another, we all have sensed that our computer has breached our privacy. A similar curiosity has led me to do some online research. I have compiled my findings as approaches to identify if my computer is being monitored.
If you follow along and have found nothing suspicious, rest assured you will be sleeping well at night.
How Can An Attacker Gain Access To Your System?
When it comes to monitoring, a computer program is always the one to do it. Malicious software gets installed on your computer all the time with or without your consent. It is likely you won’t ever remove them unless you need to.
And by that time, it may be too late before it compromises your privacy. A common way this software makes it to your computer is through file downloads.
For example, take this website.
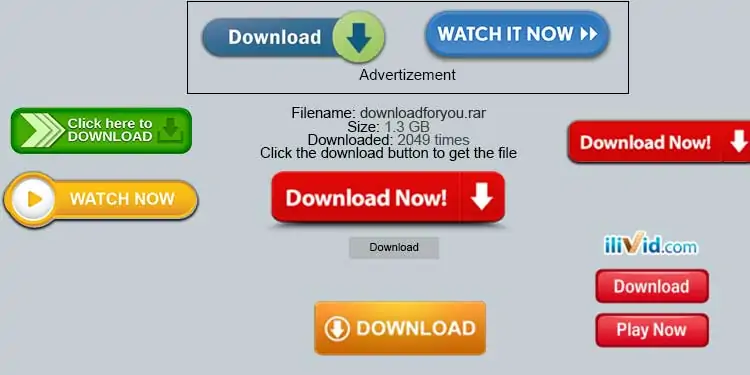
Which button would you use to download the actual file? Yes, I’d be confused too if I saw something like this. A lot of times there are fake buttons placed in websites like these. They may not download your file for you, but install a program on your PC instead.
It is possible to tell a button isn’t what you’d want by pressing it first. But would you be willing to take that chance? I mean, downloading a file shouldn’t be a challenging task for anyone. Even so, some of the times you can’t tell if you got the file you wanted, or ended up with a tracker program on your PC.
Tip : If it’s not a software you’re downloading, then the file(s) should NOT be of exe file format.
How to Tell if Your Computer Is Being Monitored
Here are 7 different ways to confirm if your computer is free from being monitored or not.
1. Monitoring processes from Windows Task Manager
- Press Ctrl + Alt + Del Key together to start Windows Security.
- Select Task Manager to open the Task Manager Window.

- If it is the minimal view, Click on More details to open the detailed view.

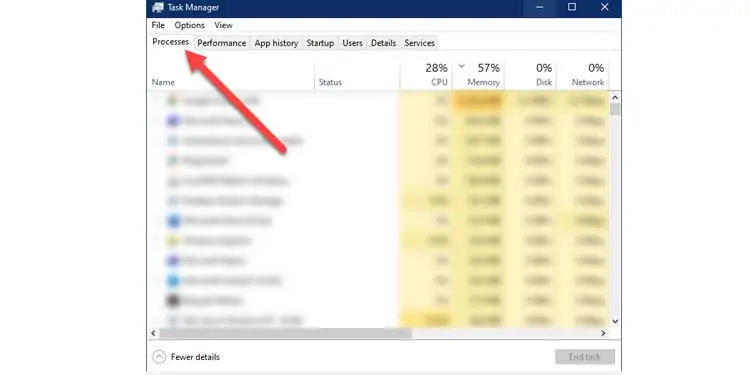
- Click on the Processes section to bring up a list of all current programs and processes.
Take a good look around. This is the surest way to familiarize yourself with the applications. Make sure nothing fishy is running.
2. Monitoring Open Ports using netstat
- Go to Start Menu and click Run.
- Type CMD and press enter to bring up the command line interface.
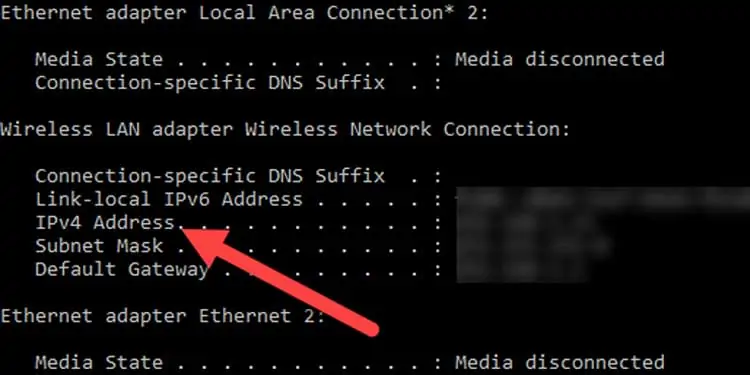
- Type the command ipconfig to display the list of network adapters.
- For each connection profile, note down the IPv4 address. No need to worry about the rest of the information.( Tip : If you run a VM software such as VMware or Virtualbox, you will see a bunch of virtual adapters. This is normal.)

- Type the command netstat -an to get a list of all listening ports and addresses.
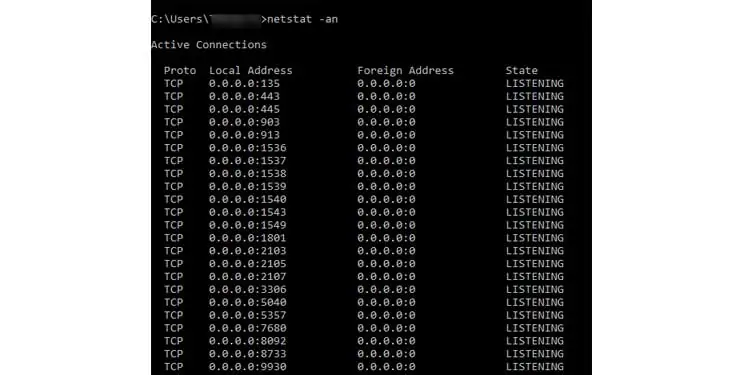
In this list, other than the ones noted in Step 4, you need to make sure that there are no new IP addresses. If there are any, it means that another PC is connected to your computer via Remote Desktop Services. Somebody is snooping around on your computer.
3. Periodic Antivirus scans
- Go to Start Menu or Click on Search bar.
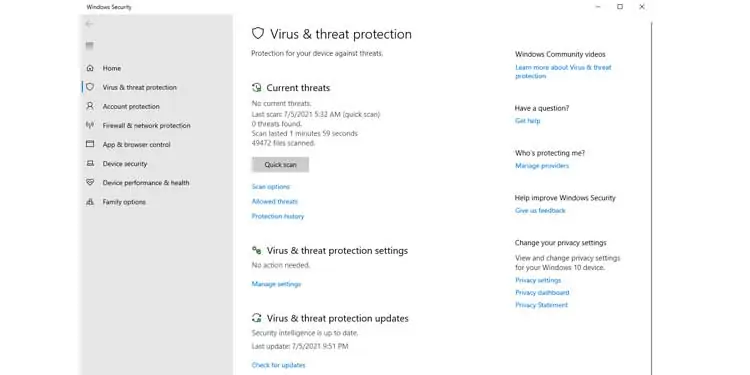
- Type ‘threat protection’ to bring up the Virus & Threat protection window.

- Click on Quick scan to perform a virus scan of your computer.
- Or, Click on Scan options. This gives you choices to perform a full scan, Custom scan among other options.
- Once it is complete, make sure that there are no suspicious files or threats found in your PC.
The built-in virus & threat protection app is pretty good at identifying threats. Yet, a lot of people opt to go for stand-alone antivirus software. These software detect monitoring programs called spywares and keyloggers.
After scanning, they are removed from the system to provide full protection all the time. Antivirus software can be of either free or paid versions. It is recommended to have a paid version from a trusted Antivirus company.
4. Investigating Recent Files
- Click on This PC from your Desktop or Taskbar.
- Click on Quick access on top left under the navigation bar to bring up Frequent folders and Recent files.
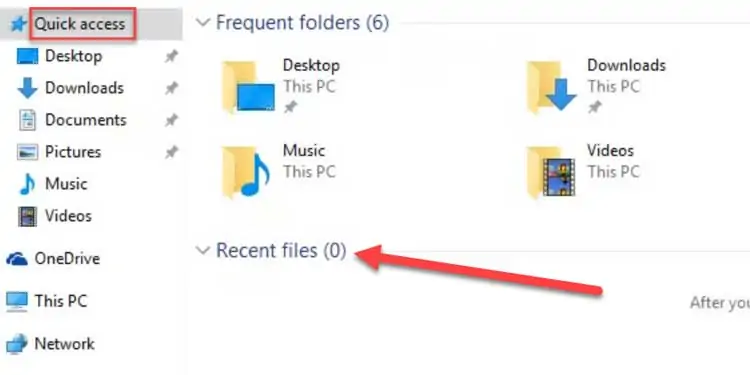
This is the most simple and quick way to identify if someone has been checking up on your file system.
The Recent files section shows you a list of the last accessed files and folders. If anything here isn’t opened by you, then it’s somebody else that accessed it on your computer.
5. Investigating Browser History
Open your internet browser and find the browser history (press Ctrl + H or Ctrl + Shift + H)
This is another quick way to see if someone hasn’t used your PC with malicious intent. The browser records all websites that were visited on your computer for a long time. Again, if anything looks unfamiliar to you, it’s likely somebody else has access to your computer.
But, it is impossible to trace using this approach if the offender used Incognito mode. Keep in mind that Incognito mode does not leave history on the browser. In any case, repeat this approach for all installed browsers and not just the ones you use.
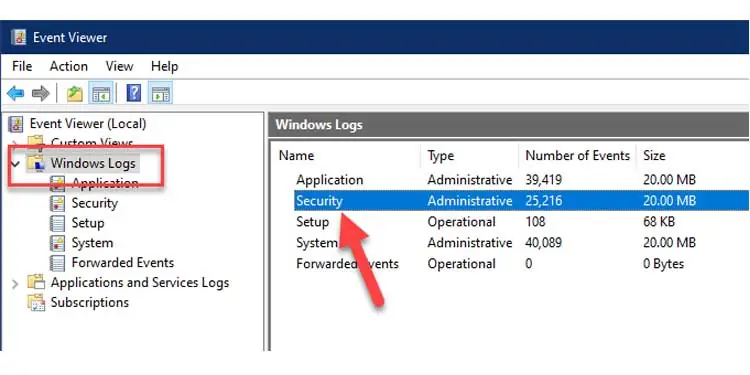
6. Auditing Login Event Viewer
You can also access the login events to see if someone remotely logs in and out of your computer. For this, do the following :
- Go to Start Menu and search for ‘Windows Administrative Tools’ to bring up a new window.
- Click on Event viewer to launch the Event viewer application.
- On the left navigation pane, click on Windows Logs. Then double click on Security to bring up all Security events.

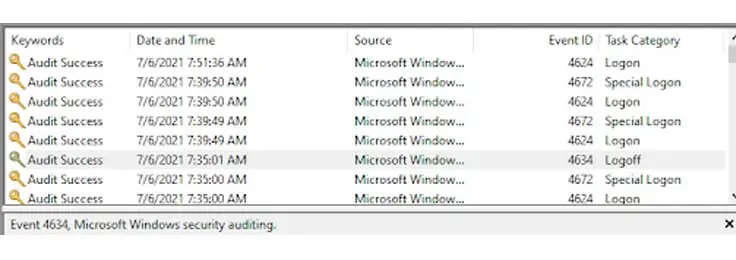
- Look for any event(s) with Task Category Logon/Logoff. You can go to a specific date and time range to make the process more helpful.

You need to look for an Administrator group login. But, It is normal to see a trail of SYSTEM and BACKUP logins. If you find anything unordinary in the logs, it means you’re in trouble. Someone is logging in and out of your system and monitoring your activities.
7. Identifying Corporate Monitoring
This is the most ‘legally ok’ type of monitoring. If you don’t own the computer you’re on, you are technically using somebody else’s computer. This somebody could be the corporate business you work for.
Businesses use many tactics to protect their company’s trade secrets and business assets. So it is natural that they install monitoring tools on the computers they own. IT Team legally has the right to install programs on the company’s PC.
It is understandable that they only do this to protect the company and its data. The application they install can be of varying types. Some may only report system resource usage. Others are capable of logging keystrokes and application activities. Some even go as far as providing remote access to the IT Team.
This does not necessarily mean that they are going to be insensitive with your personal data. Privacy concerns and standards are always practiced at a good organization.
The installed programs generally run in the foreground. Unlike a virus, they also do not attempt to conceal themselves. You’re likely to find these programs running in the taskbar or the task manager. But this can vary on the type of software.
Techradar provides an excellent list of employee monitoring applications.