When hosting a web server or a web application, you need to open port 443 (or port 80) on the server so that it can receive a web request. While port 80 relates to HTTP, port 443 corresponds to HTTPS.
According to Google’s research in 2021, over 95% of websites have been using HTTPS. It offers more secure communication than HTTP and is the de facto standard for modern web security.
If you want to understand more about this port and how it works, you need to know what a port represents first. So, let’s start!
What Exactly is a Port?
In a general sense, a port represents the connection point or interface between external and internal devices. So, in a computer network, it is a unique virtual endpoint where the network connection starts or ends. The ports can allow or restrict outbound, inbound, or both connections, and the firewall is responsible for the corresponding rules.
If you try to access another device on the network, your device will use certain ports depending on the protocol you are using to establish the connection. The protocol can be the usual communication protocol like Transmission Control Protocol (TCP)/User Datagram Protocol (UDP), data sharing protocol like File Transfer Protocol (FTP), and so on.
The port needs to be opened on the other device to establish the connection. They are associated with different services that help establish and implement the connection based on the communication protocol.
A total of 65536 port numbers are available for the different network protocols. Among them,
- System or Well-known Ports (0-1023) are pre-assigned as the default number for some well-known ports.
- User or Registered Ports (1024-49151) are unassigned ports that are available for regular users. They need to register the port at Internet Assigned Numbers Authority (IANA) to prevent duplication.
- Dynamic or Private Ports (49152-65535) are short-lived ports that are used for private services or for temporary reasons.
What is Port 443 and How Does It Relate to HTTPS?
Many web servers use Transport Layer Security (TLS) certificates to improve their security. If you try accessing such a web server using TCP protocol, the network will use an encrypted channel to send the request to, and receive data from the server. Port 443 is the default virtual endpoint of this secure channel on the web server.
Your web browser will use the Hypertext Transfer Protocol Secure (HTTPS) in the application layer to send requests and receive the data. So, port 443 is directly associated with HTTPS protocol. Some VPN or other services also use this port to bypass firewall restrictions.
TLS is a more recent version of Secure Sockets Layer (SSL), so you might still find SSL used a lot to describe security certificates. But nowadays, SSL is deprecated and only the recent versions of TLS are in use.
Most web servers now use TLS certificates as data security is of utmost concern. This is why you’ll see https:// instead of http:// in almost all URLs.
How Does HTTPS and TLS Encryption Work?
TLS technology uses a set of two keys (public and private) for encryption. Only the private key can decode the data that the public key encrypts and vice versa. Here’s the complete process of how HTTPS and TLS encryption work:
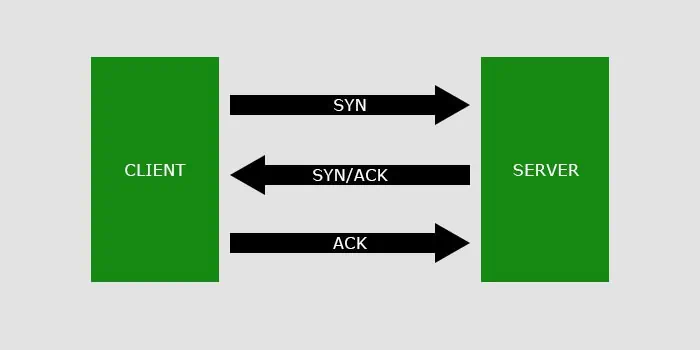
- The web browser must first establish a connection (TCP Handshake) with the web server before it can send a TCP request.
- The web browser sends a synchronization data packet (SYN) to the web server to request a connection.
- The web server responds with synchronization (SYN) along with an acknowledgment packet (ACK).
- The web browser then responds with ACK, which establishes the connection between the browser and the server.

- For HTTPS, another handshake, i.e., the TLS handshake, is necessary since the data needs to be encrypted. This step is not necessary for HTTP as they can directly begin sending application data in plain text format.
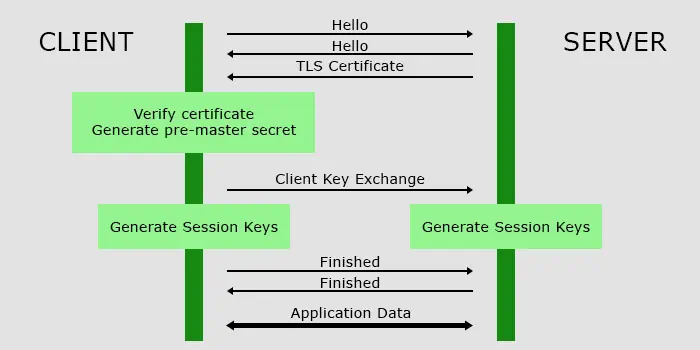
- In TLS 1.2, RSA encryption is used, which goes like this:

- First, the server and the client browser exchange “hello” messages.
- Then, the two terminals communicate their protocols, encryption standard and so on. The server also sends the TLS certificate containing the following information:
Domain namePublic keyCertificate Authority along with their digital signatureIssue and Expiration dateTLS version
- Here, the server sends the public key included in the TLS certificate to the client for the encryption/decryption process. The private key is stored only in the web server and it doesn’t share the key anywhere.
- The client verifies the TLS certificate and then creates a random byte code (pre-master secret).
- Then, it encrypts the secret code using the public key and shares it to the server. The server uses the private key to decrypt this data.
- Both clients and servers create a set of session keys using the pre-master secret.
- Then, the two terminals will send “finished” messages and they can finally begin sending application data.
- They will communicate while using these temporary keys for encryption and decryption. They remain valid for a certain period of time and expire after the session ends or the connection breaks. The same process occurs again to recreate another set of session keys.
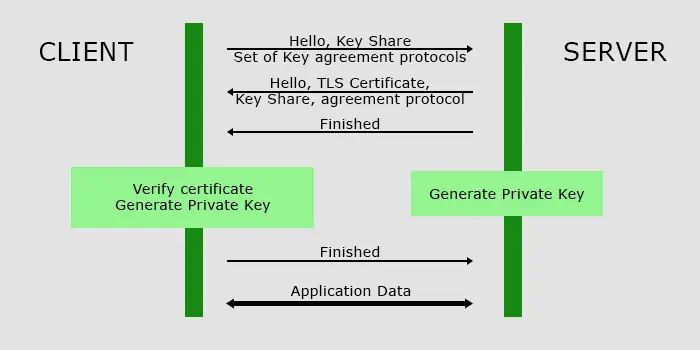
- In TLS 1.3, DHE encryption is used, which is much faster.

- The client sends a supported set of keys and key agreement protocol as well as its own key share along with the “hello” message to the server.
- The server responds with the server’s certificate, its key share, and the key agreement protocol it selects from the set after the “hello” message.
- It also sends its “finished” message since it does not need to send any more data before beginning the connection.
- The client verifies the certificate, generates the necessary encryption keys and sends the “finished” message.
- Now, both the server and the client have the necessary keys for encryption/decryption and can begin sending application data.
Web servers can use different levels (not versions) of TLS certificates along with HTTPS, depending how stringent the certificate authority (CA) is while providing the certificates.
- Domain Validation Certificates: This certificate only validates the domain ownership. It has the lowest level of validation and is only appropriate for blogs and similar websites.
- Organization Validation Certificates: The owner needs to verify personal and business details along with domain ownership while applying for these certificates.
- Extended Validation Certificates: They have the highest level of validation and the owner needs to verify exclusive rights to the domain—their physical address along with all the personal, business and domain details.
How Does Port 443 Compare to Port 80?
Like how the network sends HTTPS requests to port 443 on the web server, the HTTP requests go to port 80 by default. These HTTP requests and the corresponding data from the web server do not go through any encryption on the network. So, these data are in plain text and are highly vulnerable to external access.
Is Port 443 Important?
HTTPS dramatically improves data security as compared to HTTP. This does not mean that it is fully secure, as there are ways to exploit it, such as stealing data from browser cache or memory. However, it is the most secure protocol at this time.
Most web servers don’t allow HTTP requests and your browsers will also try to prevent you from accessing any websites through HTTP. Since HTTPS is the current standard, port 80 is not used much. As such, all web communications go through port 443.
It is possible to specify any other port as the endpoint for HTTPS communication instead of 443 on the server. But the client will also need to specify the particular port number while making an HTTPS request. So, unless a developer is testing their web servers, nobody will be using any other port as a replacement.
Should You Open Port 443?
Whenever a client makes a web request, the client device uses an available registered or dynamic port (between 1024 and 65535) to send a request to port 443 or 80 on the server depending on the protocol you use.
So, if you are setting up a web server for other people, you will need to open the 443 port for inbound HTTPS access so that they can connect to it through the internet. But it is not necessary to open the port on the client-side for any outbound access since the device will use a different open port.
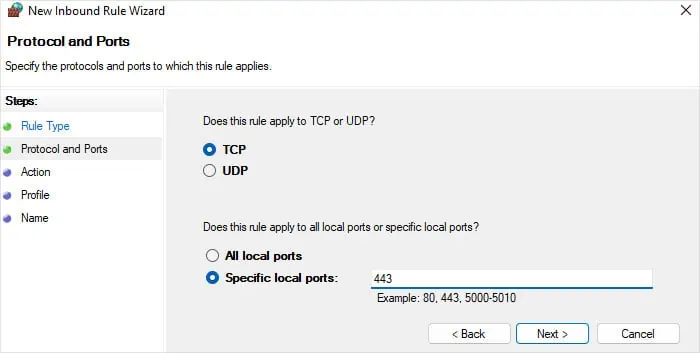
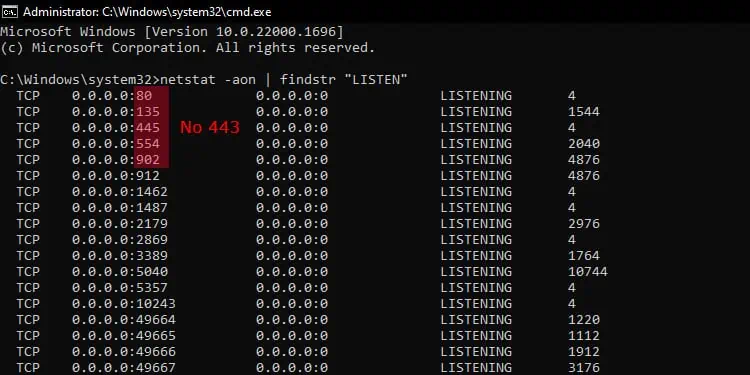
Before trying to open the port, check if it is already open using the command netstat -aon | findstr "LISTEN" on Command Prompt
If it is not open, follow the steps below.
- Open Run by pressing Windows key + R.
- Type
firewall.cpland press Enter to open Windows Defender Firewall. - Select Advanced Settings from the left navigation pane.
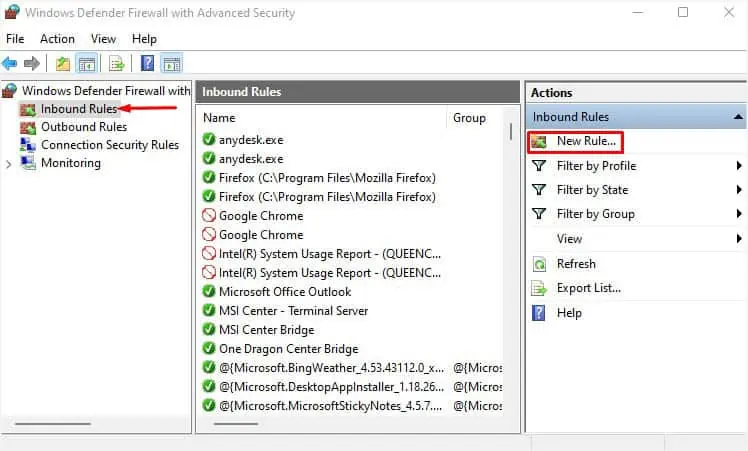
- Go to the Inbound Rules tab and click on New Rule.

- Check Port and click Next.
- Select TCP and enter
443on the Specific local ports. Hit Next again.
- Check Allow the connection and hit Next.
- Select the options per your need and click Next.
- Specify any name you want and choose Finish.