These days, we not only use Email to send messages or letters but also link bank accounts, store sensitive data, and sign up on various platforms. Hence, attackers may try hacking your account to access vital information or send/receive phishing e-mails.
Whether you’ve clicked on phishing links, had your data breached, or set an easy-to-guess password, all these can lead to your email being hacked. Once a hacker is able to access your account, they can compromise your password, send inappropriate messages to your contacts, or in the worst case, gain access to your banking information.
You won’t get a message like, “Your account has been hacked!” after your account is compromised. Instead, there are some simple methods to know if your email has been hacked, and that’s exactly what we have covered in this article.
How to Know if Your Email Has Been Hacked?
You’ve probably shared your email address with several people and companies until now. However, if an attacker gets your details, it doesn’t become hard for them to hack your account unless it is fully secured. They may use phishing, brute force attack, session hijacking, and other techniques to compromise your account.
Once your Email is hacked, you, along with your contacts, are at potential risk. These attackers may steal your credit card details, post weird things on social media, or even blackmail you!
Therefore, you should always avoid phishing links, sign out if you’ve logged in on an untrusted device, and regularly run a malware scan. This can help prevent your email from being hacked.
You Can’t Log In
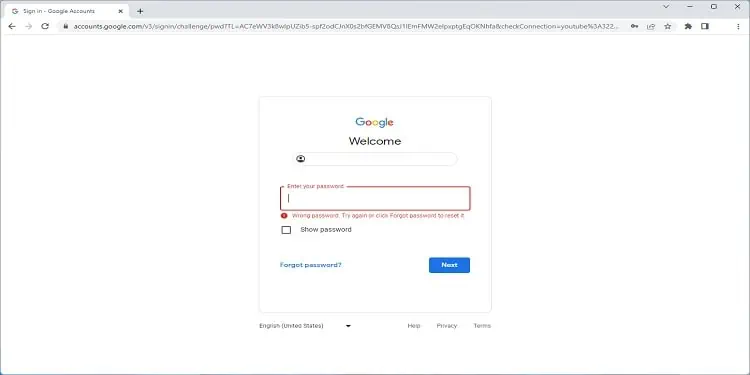
One of the common issues you may face as a victim is that the hacker doesn’t just access your account but even changes the login credentials. In such a case, no matter how often you use the old passwords, you simply can’t log in.
Some hackers even throw you out of all the connected devices, ensuring the recovery process becomes much more difficult. Moreover, these attackers may even change your recovery phone number and other credentials.
- Your e-mail address has been changed
- The account password has been changed
- Hacker has changed the recovery phone number or other settings
- Your account has been permanently deleted
In such a scenario, the only possible solution is to get to the email provider’s account recovery page and answer all the questions. The process may take a few days, depending on the provider.
Check Devices Accessing Your Account
The best way to determine if your email has been hacked is by checking all the devices accessing your account. Most providers include this feature to help improve security.
For demonstration, we will use Gmail to check and manage the devices. Other services (Yahoo, Outlook, iCloud, etc.) also have a similar feature. Kindly follow the below instructions on how to do it:
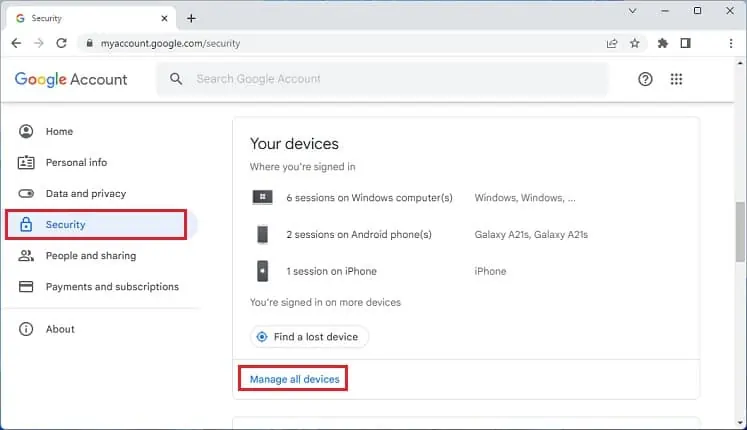
- Log in to your Google account and navigate to the My Account page.
- Next, select Security from the left pane.
- Scroll down and find the Your devices section. Here, click on Manage all devices.

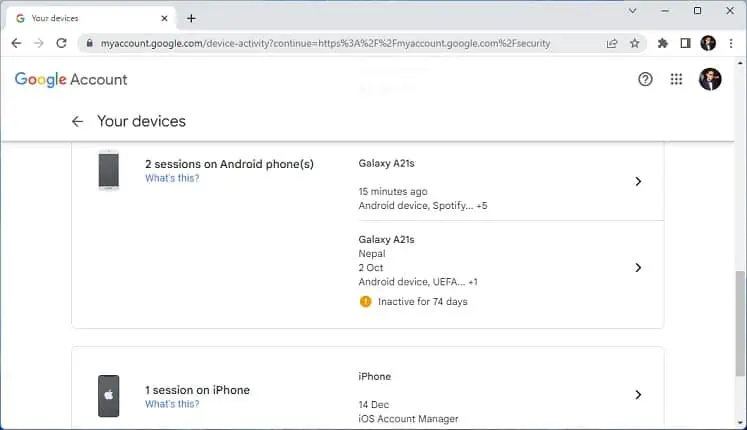
- Now, you’ll get all the sessions where your account is currently logged in (Windows, macOS, Android, iOS, etc.). Point out the suspicious device(s).

Once you’ve identified the hacker, you can remove your email connection from their device. Go through the following instruction on how you can do so on Gmail:
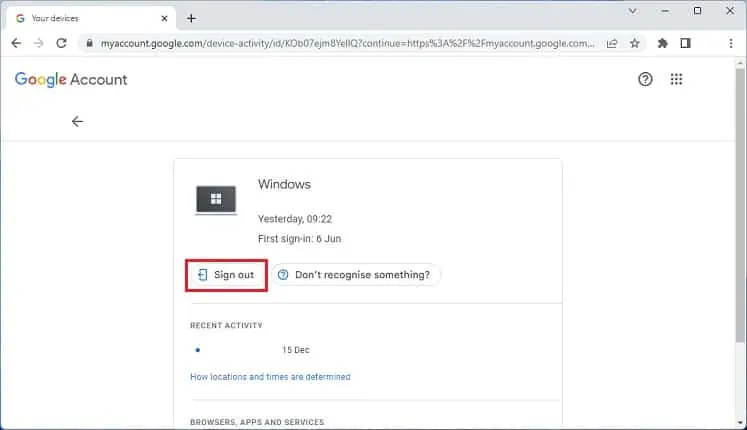
- Click on the suspicious account.
- Here, hit the Sign out button to remove your account on that device.

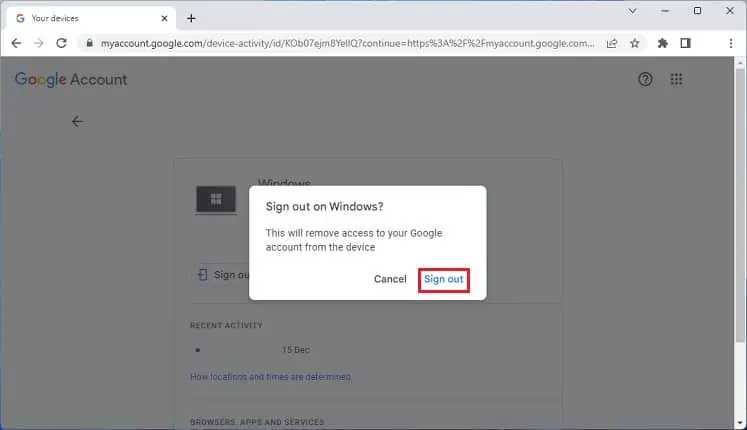
- In the confirmation dialogue box, press Sign out.

Now, the hacker won’t be able to access your account unless they reenter the login credentials. To prevent this, we recommend changing your email password as soon as possible.
You Keep Getting Password Reset Emails
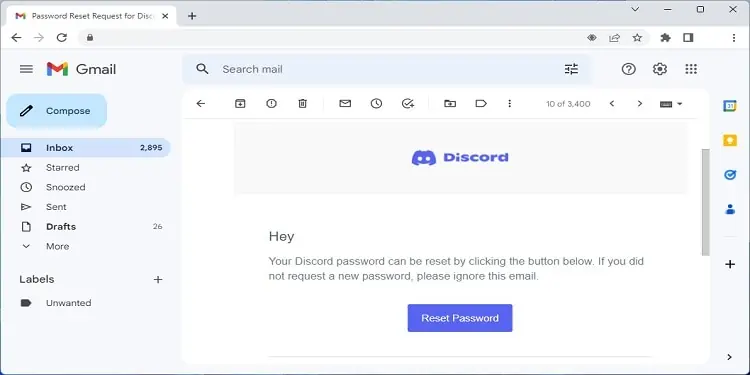
Some attackers hack your email to gain access to other connected services, like social media, online banking, and more. During the process, the hacker may try changing the account’s password, which is why you keep getting password reset emails.
In such a case, we recommend resetting both the application and email password as fast as possible. Also, you can sign out of the suspicious device to ensure that they do not re-access your email account.
- The attacker doesn’t have access to the service. So, they’re trying to reset the password to gain access.
- The attacker has already hacked the service but wants to reset the login credentials, so you don’t regain access.
- The attacker has already crossed the limit of login attempts. So, the service triggers the reset password message on the email to notify you about suspicious activity.
Strange Messages in Sent Folder
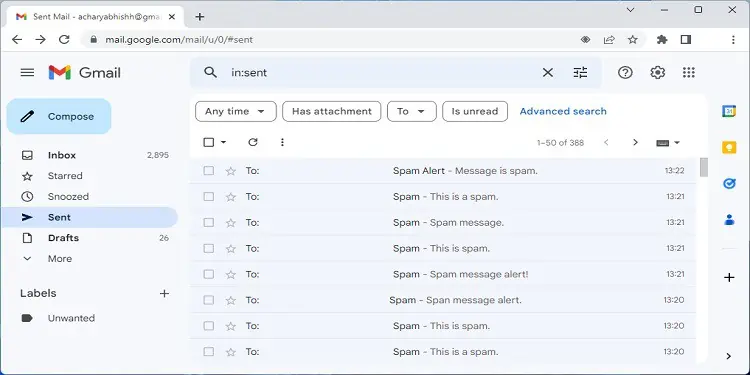
Most hackers compromise users’ accounts to send fraudulent emails to others. They take control of your mailing address, and you won’t even notice that they’re sending inappropriate messages to your contacts.
- Gain access to their login credentials to hack them as well
- Install malware on their devices
- Hoping to get banking or credit card details
- Trying to defame you
Nonetheless, you can keep track of the Sent folder to know whether your email has been hacked. If you find strange messages you do not remember forwarding, it’s a definite sign that your account is already compromised.
Therefore, it’s a good idea to keep changing your email password regularly. Also, we discourage using the same passcode for every account, as doing so might make the hacker aware, and they will likely compromise all the other services too. For your comfort, we have prepared a detailed guide on what makes a good and strong password.
One thing that makes it difficult is that the attacker can delete all the emails at once. If that’s the case, we recommend checking the Bin folder that might still have those fraudulent emails.
Complaints From Others
Tech-savvy users can easily differentiate between legitimate and fraudulent emails. If you have such people in the contacts, they’ll likely communicate with you regarding these messages. Indeed, if you receive multiple complaints, it’s a clear indication that your email has been hacked.
Likewise, you can also check your alternative email to see if the primary account has been sending any spam messages. If you notice any, you should immediately make your friends and families aware of the issue.
Suspicious Activities With Your Account

Some hackers do not just compromise your email and send fraudulent messages; they even change your account settings or view your personal data.
- Weird posts on social media
- Important emails are deleted
- Unread emails are read
- Changes to your critical security settings (recovery phone number, email address, login credentials, etc.)
- Unfamiliar changes in other products
Most of us sign up on social media using our emails. Hence, they remain one of the easiest to hack. If you’ve noticed someone has liked and commented something unusual or published weird posts, this is a definite sign that you are at risk.
Likewise, some hackers may access and delete your important emails. This could be one of the reasons your Gmail messages are missing. They do not just gain access to your personal information but even tend to modify them.
If you notice that your name, phone number, or other settings are tweaked, there’s no doubt that your email has been hacked. In this scenario, an attacker is probably trying to become a legitimate user of that account.
Lastly, some email providers, like Google, lets users connect to several of their products (Google Drive, YouTube, Blogger, etc.) with the same mailing address. So, if you notice any changes on them, it’s a possible sign that your email has been compromised.
Check if Your Account Data Has Been Breached
You can even check if your email data has been breached using third-party resources, like Have I Been Pwned?, Firefox Monitor, etc. These tools scan your account and identify if your private information has been leaked or compromised.
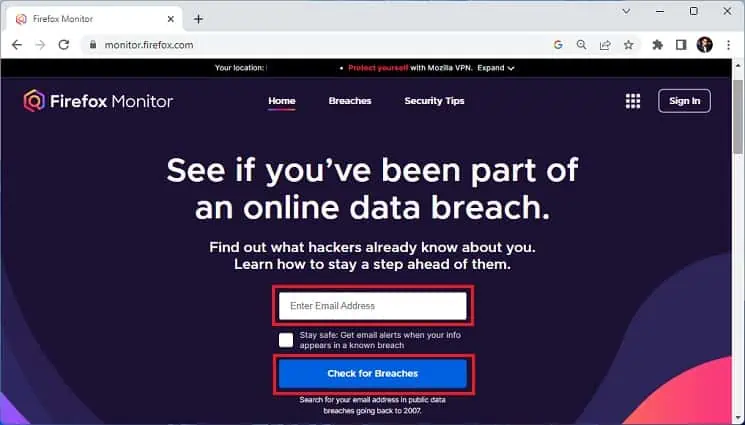
All you have to do is input your email address, and they provide results within a minute or so. Here’s a quick demonstration of how you can do this on Firefox Monitor:
- Firstly, visit the official Firefox Monitor website.
- In the Enter Email Address field, input your valid email.
- Click the Check for Breaches button and wait until the scan is complete.

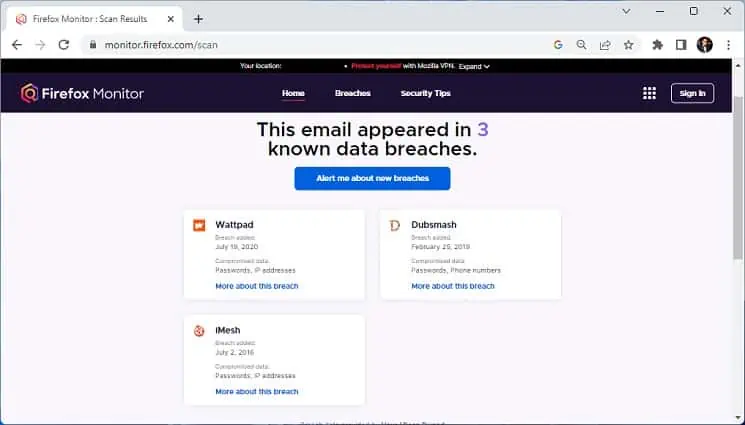
- Now, you should get the details of whether your data has been breached, as shown in the figure below.